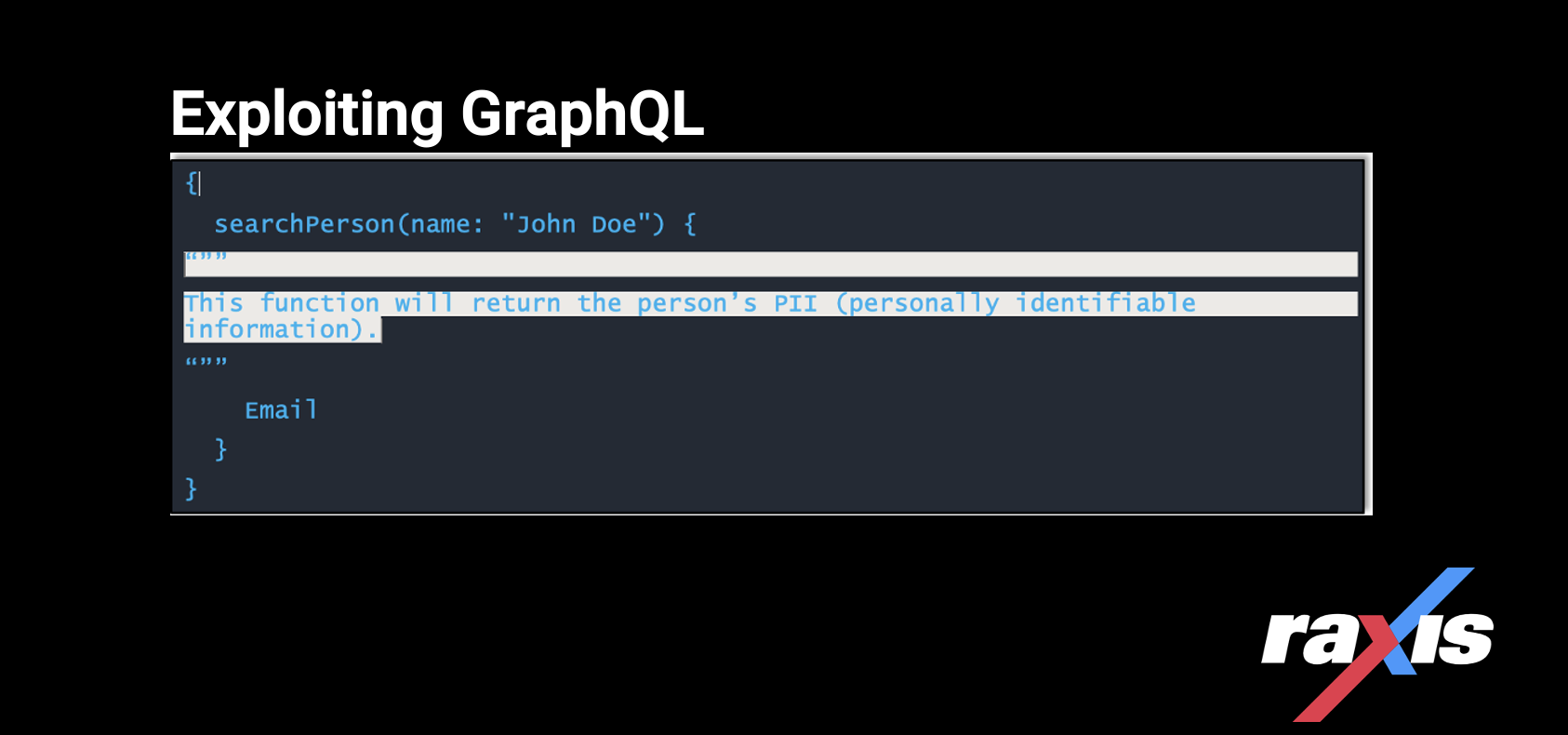
Log4j: How to Exploit and Test this Critical Vulnerability
In this article, Raxis’ CEO Mark Puckett describes how penetration testers and ethical hackers can[…]
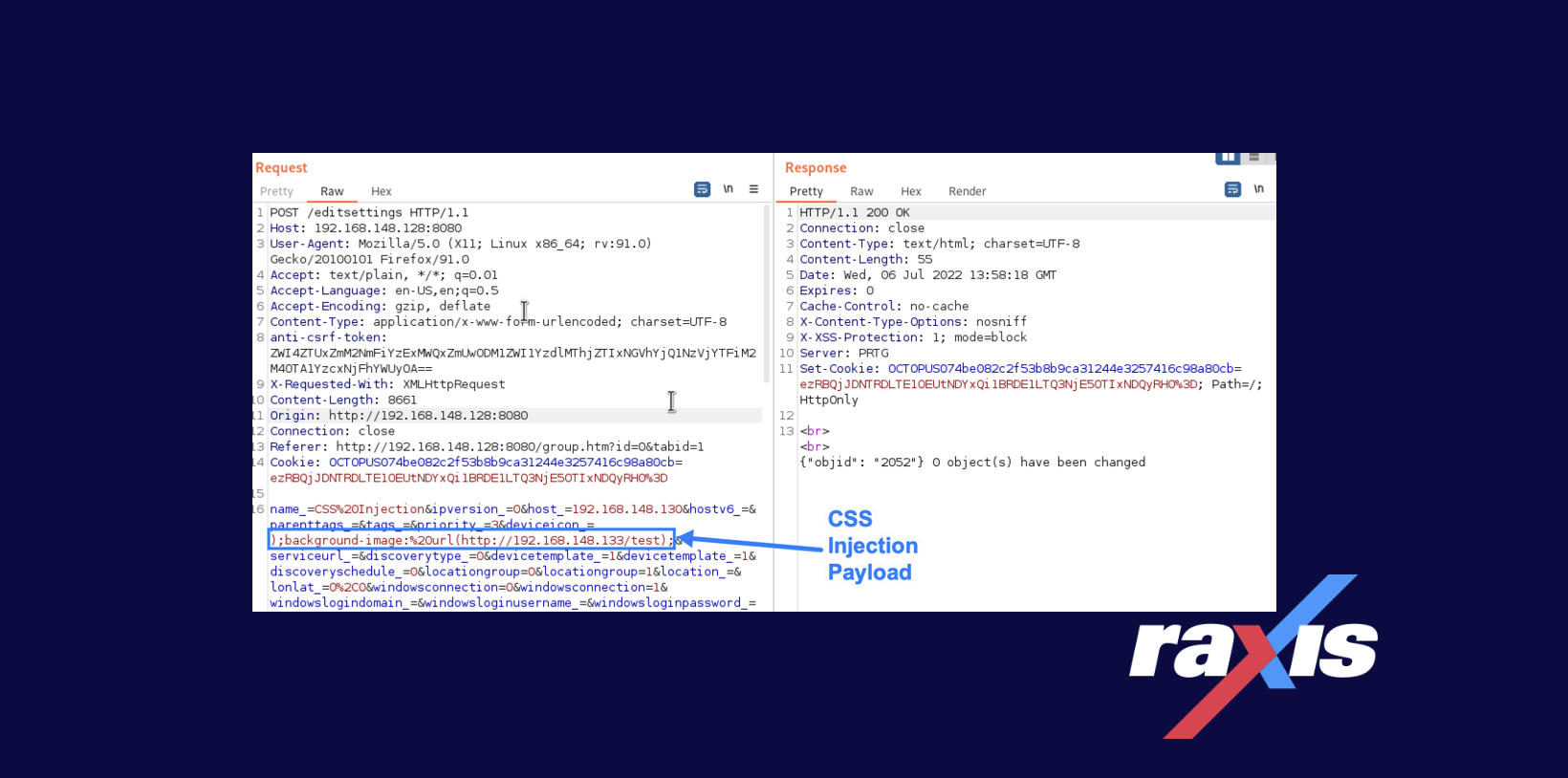
CVE-2022-35739: PRTG Network Monitor Cascading Style Sheets (CSS) Injection
This CSS vulnerability, discovered by Raxis lead penetration tester Matt Mathur, lies in a device’s[…]

Why Mutual Assured Destruction is an Incomplete Cyber Defense Strategy
Is the threat of full-scale retaliation enough to prevent large-scale cyberattacks? Raxis’ COO Bonnie Smyre,[…]

LDAP Passback and Why We Harp on Passwords
LDAP passback exploits are easy when companies fail to change default passwords on network devices[…]

SonicWall Patches Three Zero-Day Vulnerabilities
Cybersecurity company SonicWall has released patches for three zero-day vulnerabilities that are currently being exploited.

IKE VPNs Supporting Aggressive Mode
Raxis’ COO Bonnie Smyre breaks down what IKE VPNs are, what Aggressive Mode means, and[…]

Ransomware – What you can do to avoid being a victim
Raxis VP of Business Development Brad Herring discusses ways to protect your company from ransomware[…]